Skip to content
Using openSSL certificates in NodeJS
— notes, nodejs, security — 1 min read
# Install
1npm install --save express morgan nodemon# Steps for SSL certificate generation
Generate a private key
1openssl genrsa -out key.pem2Generating RSA private key, 2048 bit long modulus (2 primes)3..............+++++4.............................+++++5e is 65537 (0x010001)Create a CSR(Certificate Signing Request) using private key. Here it will few questions like country code, state, city, organization name, organization unit, common name/hostname, email address and challenge password. You can skip by pressing enter.
1openssl req -new -key key.pem -out csr.pem2You are about to be asked to enter information that will be incorporated3into your certificate request.4What you are about to enter is what is called a Distinguished Name or a DN.5There are quite a few fields but you can leave some blank6For some fields there will be a default value,7If you enter '.', the field will be left blank.8-----9Country Name (2 letter code) [AU]:IN10State or Province Name (full name) [Some-State]:Tamil Nadu11Locality Name (eg, city) []:Chennai12Organization Name (eg, company) [Internet Widgits Pty Ltd]:bobbydreamer.com inc13Organizational Unit Name (eg, section) []:Tech14Common Name (e.g. server FQDN or YOUR name) []:bobbydreamer.com15Email Address []:bobby.dreamer@gmail.com1617Please enter the following 'extra' attributes18to be sent with your certificate request19A challenge password []:20An optional company name []:Generate self-signed certificate using CSR. Here
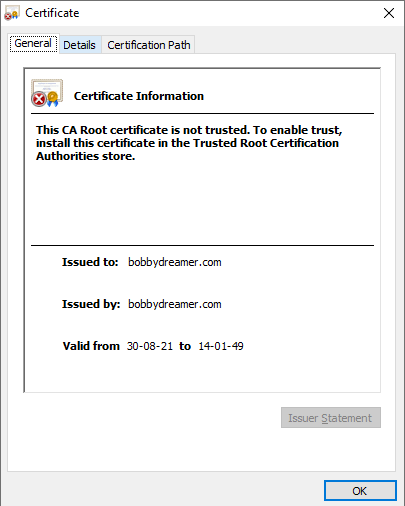
x509is a standard for defining public key certificate.1openssl x509 -req -days 9999 -in csr.pem -signkey key.pem -out cert.pem2Signature ok3subject=C = IN, ST = Tamil Nadu, L = Chennai, O = bobbydreamer.com inc, OU = Tech, CN = bobbydreamer.com, emailAddress = bobby.dreamer@gmail.com4Getting Private keyCSR file is no longer required. It can be deleted
1rm csr.pem
if you want to extract public key from private key, you can use below command.
1openssl rsa -in key.pem -pubout -out public.pem# Verifications
1openssl req -text -in csr.pem -noout -verify2
3verify OK4Certificate Request:5 Data:6 Version: 1 (0x0)7 Subject: C = IN, ST = Tamil Nadu, L = Chennai, O = bobbydreamer.com inc, OU = Tech, CN = bobbydreamer.com, emailAddress = bobby.dreamer@gmail.com8 Subject Public Key Info:9 Public Key Algorithm: rsaEncryption10 RSA Public-Key: (2048 bit)11 Modulus:12 00:c0:eb:fc:de:87:cf:ac:56:87:26:9d:04:4a:f8:13 1f:db:0c:9f:ad:8d:2b:66:d8:60:cd:35:82:05:a3:14 ff:4c:19:39:27:e0:bf:99:a6:6d:5b:8a:57:8a:12:15 45:ab:d5:94:d8:11:71:cf:78:19:21:e1:86:2f:f8:16 07:8e:72:be:e1:59:f5:6a:99:29:b1:89:7a:d8:91:17 a4:68:b1:86:0e:0a:a8:72:99:51:a7:e6:92:d2:52:18 d4:d4:02:3c:e0:a0:c6:0a:e1:de:52:76:15:ba:cc:19 81:33:86:09:bd:3e:51:19:be:65:cd:51:67:a8:7b:20 36:9e:56:b9:17:46:db:ee:e1:c6:a4:47:a9:9b:1a:21 56:6b:9a:41:de:1f:11:80:fa:7d:58:42:29:c7:5d:22 ca:6f:a8:7d:98:b3:06:ef:ca:62:73:cb:a9:46:69:23 a8:36:de:19:76:f1:4f:2f:6f:47:32:70:f2:93:bf:24 5a:71:db:75:38:4b:7e:a5:06:56:7e:e2:a8:1c:79:25 4e:10:23:24:8b:c2:7f:d7:11:3a:d3:d7:f0:ae:94:26 ea:c0:e2:51:c4:06:e2:c9:e7:63:6a:d6:f4:b9:59:27 5e:47:ad:e9:df:bc:2f:c6:b6:3d:93:b0:02:44:d9:28 a1:e7:92:99:8a:87:5c:95:f5:84:8d:47:01:66:5c:29 90:a130 Exponent: 65537 (0x10001)31 Attributes:32 a0:0033 Signature Algorithm: sha256WithRSAEncryption34 af:d4:ff:a6:b4:cf:2e:b3:13:29:03:bc:3f:7b:30:b8:27:ee:35 75:33:06:15:0f:97:3b:a2:1a:5e:6c:22:84:bd:d7:db:ff:7e:36 fd:cb:61:da:cf:ed:4d:63:72:37:4f:44:0f:16:6c:eb:a6:9a:37 7f:1a:08:19:28:80:0f:ae:e6:01:a4:db:2f:df:df:68:fb:b6:38 a2:ce:96:1a:19:28:6f:e5:d7:04:0d:e5:ba:01:67:76:90:21:39 1f:93:d9:df:68:a0:5d:ed:7f:f4:9c:20:9c:15:1a:cf:9b:1d:40 3c:c7:e5:87:5c:23:22:f7:26:36:38:bc:0e:5f:41:c0:df:9c:41 65:ee:33:e2:3d:5f:f3:91:f9:de:66:11:d0:16:d5:6e:cf:3a:42 43:4e:cf:af:51:00:a6:ed:bb:8d:93:54:5d:ee:ac:f8:ac:8b:43 be:d5:47:50:2e:8b:75:38:e8:32:db:14:ba:d0:e9:52:de:e8:44 7f:35:fe:b7:18:16:26:e2:28:d0:24:32:0c:11:05:b4:ed:4e:45 59:5e:06:a3:b2:1e:b8:95:1d:0f:7b:36:00:c0:f5:d6:b1:af:46 5d:5d:84:75:be:4d:19:8e:56:88:60:61:8e:65:c9:2e:7f:49:47 99:05:8f:cf:6f:c3:9a:b5:2e:23:90:f2:a3:1c:07:33:39:04:48 ed:2e:1d:5f# NodeJS Program
1const express = require('express')2const https = require('https')3const path = require('path')4const fs = require('fs')5
6const app = express()7
8const options = {9 key: fs.readFileSync(path.join(__dirname, 'certs', 'key.pem')),10 cert: fs.readFileSync(path.join(__dirname, 'certs', 'cert.pem'))11};12
13const sslServer = https.createServer(options, app)14
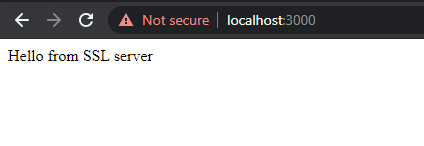
15app.use('/', (req, res, next) => {16 res.send('Hello from SSL server')17})18
19sslServer.listen(3000, () => {20 console.log('Secure server 🔑 on port 3000')21});